The availability of business-critical services is essential – and not just to avoid loss of revenue. Reliability and availability of services also strengthen the company’s reputation in the market and contribute to sustainable business success. The increasing number and diversity of Distributed Denial of Services (DDoS) attacks, therefore, present service providers and enterprises with a challenge: In addition to securing their infrastructure, many customers also expect their services to be protected against DDoS attacks.
DDoS is not a new phenomenon, and it became widely known through the volumetric attacks of the early 2000s. Due to the armament of attackers and diversity of threats, much more needs to be considered when protecting businesses against these attacks today. Even Next-Generation Firewalls (NGFW) do not provide adequate protection at this point, and they are often themselves the target.
What are Distributed Denial of Service (DDoS) attacks?
The aim of a Distributed Denial of Service (DDoS) attack is to shut off one or more online services, which are connected to the Internet. The affected Internet connection, network devices or application receives so many data packets that it’s not able to continue with regular work. Criminals aggregate multiple compromised computer systems (botnet) as a source for sending data packets to generate the highest number and most complex types of DDoS attack traffic as possible.
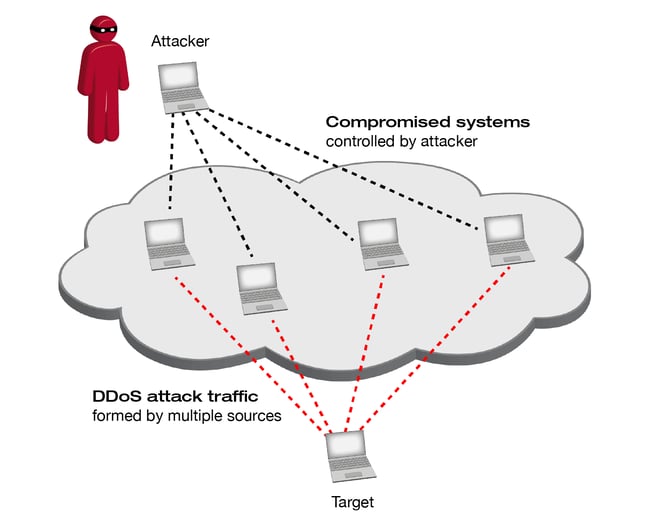
These compromised systems could be personal computers, but also devices that are part of the Internet-of-Things (IoT) like surveillance cameras, Smart-TVs or other Internet-connected devices, which are not adequately protected against abuse.
The rapid rise in the amount of IoT devices within the consumers market results in new and effective DDoS botnets like the Mirai IoT botnet in August 2016. The Mirai botnet self-propagating worm infected hundreds of thousands of vulnerable IoT devices, resulting in 2016’s highest DDoS attack which exceeded over 1 Tbps.
DDoS – State-exhaustion, volumetric and application layer attacks
When we talk about DDoS attacks, you should know that we have three types of offences: a) state-exhaustion, b) volumetric and c) application layer attacks:
a) A TCP state-exhaustion attack aims to crash stateful devices like firewalls, Intrusion Detection or Prevention Systems (IDS; IPS) or Load Balancers. These devices are called stateful because they are using tables to collecting information about, e.g. connection details like IP addresses, ports and timestamps. The memory for these tables is limited, and even high-performance devices capable of handling millions of connections are vulnerable to this kind of attack.
b) A volumetric attack is about causing congestion through consuming as much of the bandwidth of a target’s networking channels as possible. That means an attacker sends a large number of packets towards his victim so that the available bandwidth gets filled with attack traffic, and regular traffic gets delayed or even dropped. Within the last two decades, the size of volumetric attacks increased from a range of multiple 100 Mbps in the early 2000s to today’s over 1 Tbps.
c) An application layer attack aims at harming a service on the application layer. An easy example is an attacker who continuously tackles a website functionality (e.g. submitting a search form) where he knows that it causes database processing so that the underlying web service is busy with processing the significant number of requests and can’t deliver to other customers anymore. This kind of attack is very effective and hard to detect and mitigate as they run at a low-traffic rate. Application layer and infrastructure attacks are best-mitigated on-premise.
Do you know about NTP amplification attacks?
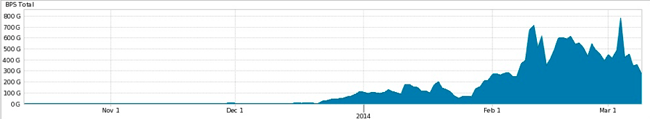
Even Network Time Protocol (NTP) servers, designed to synchronise the clock of your computer or any Network device within your infrastructure accurately, can be exploited as a part of a volumetric DDoS attack. According to NETSCOUT ARBOR, a vendor of industry-leading DDoS and Network Visibility solutions, NTP-based attacks remain as one of the most commonly used DDoS technique for reflection/amplification attacks. Increasing NTP traffic has been recognised by the ARBOR Security Engineering and Response Team (ASERT) since 2013 as you can see in the figure below.
NTP traffic tracked by Arbor’s Security Engineering and Response Team (Quelle)
NTP amplification attacks are reflection-based volumetric DDoS attacks where an attacker exploits an NTP server’s functionality by sending a command with a spoofed source IP address – which is the attacker’s target – to the server. The NTP server replies with a list of addresses of devices the server has interacted with and sends this information to the forged source IP address.
We are speaking about an amplification attack because compared to the attacker’s initially transmitted command, the NTP server’s response is significantly bigger. In addition to this, the attacker sends the initial message to multiple vulnerable NTP servers, so that all reactions together form the DDoS attack traffic. NTP servers which have a particular functionality enabled or are running with an old version are vulnerable to this kind of attack. Mitigation of this type of attack is challenging because it’s hard to filter legitimate traffic from valid servers.
Complexity – dynamic multi-vector attacks
The problem with today’s DDoS attacks is that mostly they come with a dynamic mixture of state-exhaustion, volumetric and application layer attacks, which is called a multi-vector attack. An attacker would run multiple attack types at the same time or alternately, which makes it hard to defend. ARBOR’s 13th annual Worldwide Infrastructure Security Report (WISR) shows that 59% of service providers and 48% of enterprises have already experienced multi-vector attacks on their networks. That’s why DDoS attacks remain the primary concern for 88% of the service providers for 2018.
Multi-vector attacks are also often used as a “smokescreen”, which means that an attack is part of an advanced threat campaign to hide the stealing of confidential data or intellectual property. To have adequate protection against DDoS, you will need a solution that can protect against all types of attacks – i.e. it is not enough to defend only against volumetric attacks. Devices like firewalls or IPS are not able to do this because – as described earlier – they are themselves vulnerable to state-exhaustion attacks. This means you need a solution designed explicitly for DDoS protection.
Xantaro helps to defend the availability of your services
Xantaro provides a comprehensive service spectrum around DDoS technologies with planning, the development and design of a customer-specific solution, installation and implementation into our customers’ infrastructures, and excellent operational support and maintenance services.
As a vendor-independent Service-Integrator, we work together with the best technology partners, continuously searching for useful components and products. Our solution is a “Lego-brick box” approach, which enables us to cover today’s relevant requirements and trends, bearing in mind that there cannot be just one overall solution which fits every customer infrastructure and business case. Xantaro’s strength is that we combine several solutions to cover our customers’ requirements.

All these actions need to be backed by continuous threat intelligence to stay abreast of the latest threats – being up-to-date enables you to defeat the newest threats. Within our XT³Lab infrastructure, we have multiple solutions available for advanced Proof-of-Concept tests tailored to the needs of our customers, and designed to troubleshoot issues within our customers’ production networks or advanced training.
Share your thoughts with us!
Leave a comment using the form below and let us know what you think.
.png?width=300&height=300&name=Design%20ohne%20Titel%20(7).png)