Both OpenFlow Switches are programmed with a specific set of Flows.
Switch1 has three Ports, one upstream to the network, one downstream to the scrubber, and a third one for the return traffic. There are two flows programmed per attacked IP address.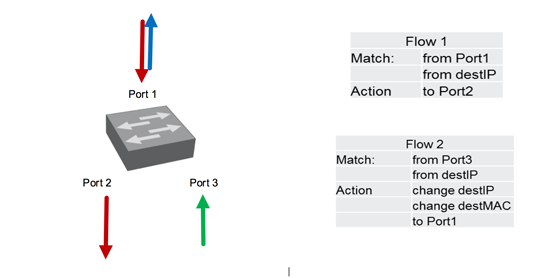
- Flow1: Take everything incoming on Port1, which has a specific destination IP (attacked IP), and send it to Port2
- Flow2: Take everything incoming on Port1, which has a specific destination IP (attacked IP), and send it to Port1, but first make some modifications. We will rewrite the destination MAC address and the destination IP address.
Changing the destination IP address is part of the trick (transform green traffic to blue traffic) the new (blue) destination IP address is temporary.
Changing the destination MAC address is done because most Routing Platforms will not accept a Packet coming in with a foreign MAC address. As the Router itself send the traffic down to the first OpenFlow Switch and (depending on scrubber implementation) nothing has yet changed the destination MAC, it would probably be discarded if left unchanged.

Switch2 has only on Port and traffic is hair pining (going in and out on the same interface).
There is only one flow programmed on this switch.
- Flow3: Take everything incoming on Port1, which has a specific destination IP (attacked IP), and send it back out Port1, but first make some modifications. Once again, we will rewrite the destination MAC address and the destination IP address.
We will transform blue traffic back to green traffic; we do so by changing the temporary blue IP back to the original green IP. Again, we need to adjust the MAC address as well.
How do the switches know which IP/MAC addresses to match and rewrite? We will cover that in a bit.
How does the network know what to forward?
There are three things we need to achieve:
1 – Make the network aware of how to send traffic to the scrubber
2 – Make the network aware of how to send blue traffic to the customer part
3 – Enable the network to receive Routing Information for Off-Ramping
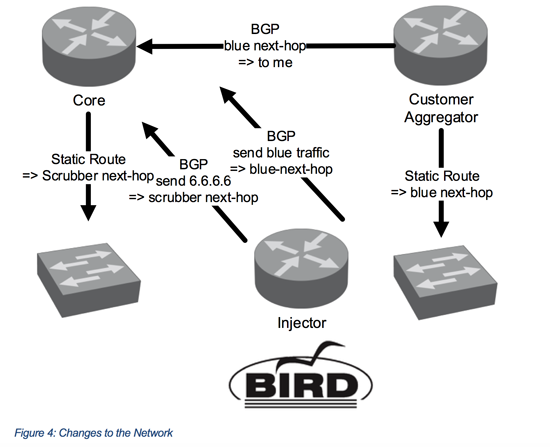
Figure 4 illustrates what the network needs to know.
First, we setup a BGP session between the Injector and the existing network. In case of an attack, this session will inform the network about two things:
- Send red attack traffic (destination 6.6.6.6 in this case) to the scrubber next-hop
- Send blue traffic (temporary IP) to the blue next-hop
Now we need to make sure that the network knows about the scrubber and blue next-hops IPs. For that, we create two static routes:
- Send scrubber next-hop IP to the interface that connects the OpenFlow Switch1
- Send blue next-hop IP to the interface that connects the OpenFlow Switch2
Some Routing Platforms cannot easily point static routes to interfaces, in that case, we need to provide workarounds e.g. by using a static IP/MAC mapping, but we will not cover that here.
As a last step, you need to make sure that the Core Part knows how to reach the blue next-hop. You can achieve that by redistributing the static route to BGP or your IGP (ISIS/OSPF) in the Customer Part or even use static routing depending on the existing network.
The Injector is running an open source routing daemon, how it knows when and what IP addresses to announce will be covered in Part 3…The Brain
Part 3 to follow…The ‚Brain‘ & the Real World Check
Share your opinion with us!
Your perspective counts! Leave a comment on our blog article and let us know what you think.
.png?width=300&height=300&name=Design%20ohne%20Titel%20(7).png)
